Hi everyone today we will see a detailed guide on Aircrack-ng Tool In Kali Linux and also i wll perform all command in my Linux machine ang giving you a live tutorial.
When it comes to check security of our Wi-Fi wireless network Aircrack-ng is one of the best tool to pentest our Wireless connections. Aircrack-ng is a simple tool present already in our Linux machine if not present then kindly update the Linux machine.
What is Aircrack-ng?
Aircrack-ng is a set of tools designed specially for testing or auditing our wireless networks. It works by capturing network packets and then try to crack WEP,WPA, and WPA2 passwords through various techniques including dictionary attacks.
If you are Termux User then read this post : How to install Aircrack-NG in Termux
Some common features include:
- Monitoring: Captures packets from the network.
- Attacking: Decrypts passwords.
- Testing: Checks the network’s integrity.
- Cracking: Cracks WEP and WPA keys.
Requirements for Using Aircrack-ng
Before going deep into how to use Aircrack-ng tool in linux its important to know the requirement of this tool:
- Kali Linux Installed: You must have Kali Linux installed either on your system or as a virtual machine.
- Compatible Wireless Adapter: A wireless adapter that supports monitor mode and packet injection is necessary.
- Basic Networking Knowledge: Understanding Wi-Fi standards and how wireless networks function will make the process easier.
- Root Privileges: Running Aircrack-ng typically requires root access.
Step-by-Step Guide: How to Use Aircrack-ng Tool in Kali Linux
Step 1: Installing Aircrack-ng tool if not installed.
Aircrack-ng comes pre-installed with kali Linux if for some reason it’s not installed or you’re using other linux distribution you can install it by typing the below commands.
sudo apt-get update
sudo apt-get install aircrack-ngCheck if the tool is successfully installed or not.

aircrack-ng --helpStep 2: Now we have set the monitor mode in our Wi-Fi adapter.
To start pentesting firstly we need to change our adapter in monitor mode to capture all packets in air. run below command to check our wifi adapters name.
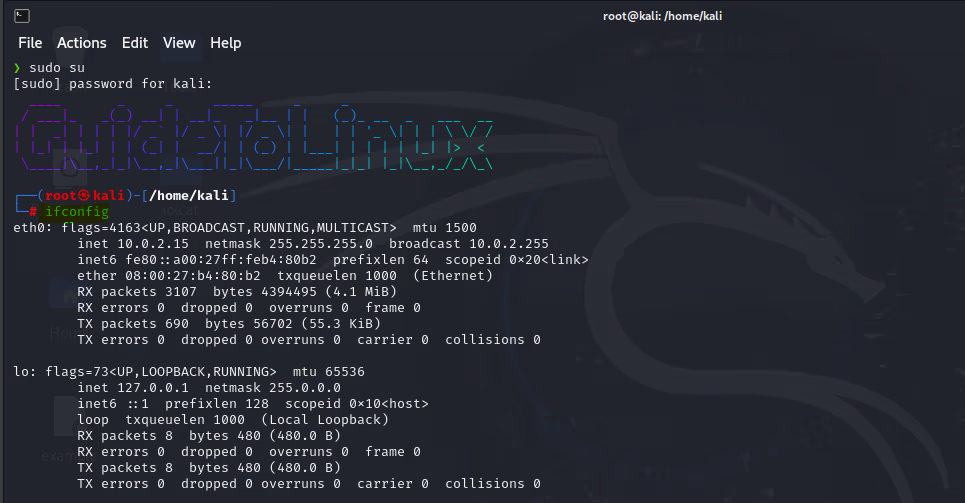
ifconfigAfter confirming the name let’s run the below command to change the mode.
sudo airmon-ng start wlan0Replace wlan0 with your interface name. This command will create a new interface, usually named wlan0mon
Step 3: Now let’s start Capturing the Packets.
With monitor mode enabled, you can now capture data packets from nearby wireless networks:
sudo airodump-ng wlan0monThis will display all nearby Wi-Fi networks, along with their essential information like the ESSID (network name), BSSID (network identifier), and encryption type.
Step 4: Now let’s start Targeting a Network.
Once you’ve identified your target network, you can focus your packet capturing on that specific network:
sudo airodump-ng --bssid [BSSID] --channel [CHANNEL] -w capture wlan0mon- Replace [BSSID] with the network’s BSSID.
- Replace [CHANNEL] with the channel number.
- The -w capture part saves the captured data into a file called capture.
Step 5: Now Let’s Deauthenticate Clients (Optional)
To speed up the process of capturing a WPA/WPA2 handshake, you can deauthenticate a connected client. This forces the client to reconnect, allowing you to capture the handshake:
sudo aireplay-ng --deauth 10 -a [BSSID] wlan0monThis command sends 10 deauthentication packets to the target network.
Step 6: Now final steps to crack password to check our password strenght & security.
Once you have captured the handshake, you can now proceed to crack the password using a dictionary attack:
aircrack-ng -w [wordlist] -b [BSSID] capture-01.cap- Replace [wordlist] with the path to your password dictionary file.
- Replace [BSSID] with the target network’s BSSID.
- Replace capture-01.cap with the name of the file containing the captured handshake.
A Table of Common Aircrack-ng Commands
| Command | Description |
|---|---|
airmon-ng start wlan0 | Puts the wireless adapter into monitor mode. |
airodump-ng wlan0mon | Displays nearby Wi-Fi networks and their details. |
airodump-ng --bssid [BSSID] --channel [CHANNEL] | Captures packets from a specific network. |
aireplay-ng --deauth 10 -a [BSSID] wlan0mon | Sends deauthentication packets to a network. |
aircrack-ng -w [wordlist] -b [BSSID] capture.cap | Attempts to crack a Wi-Fi password using a dictionary attack. |
Conclusion
In this post we have successfully learned how to use Aircrack-ng tool in our kali Linux machine also I have share some live tutorials screenshots. If you are facing any issue then let me know I will try to resolve your issue by providing some troubleshooting guides. Thanks for reading my post.
FAQs
Is using Aircrack-ng legal?
Yes, but only if you are using it to test the security of networks you own or have permission to test. Unauthorized access to networks is illegal and unethical.
Can Aircrack-ng crack WPA3 passwords?
As of now, Aircrack-ng is designed to crack WEP, WPA, and WPA2 passwords. Cracking WPA3 is extremely difficult and typically requires different tools and techniques.
What is a wordlist, and where can I find one?
A wordlist is a file that contains a list of potential passwords. There are several publicly available wordlists, such as rockyou.txt, which can be found online or through Kali Linux by navigating to:
/usr/share/wordlists/
Can I use Aircrack-ng without a wireless adapter?
No, you need a wireless adapter that supports monitor mode and packet injection to capture the necessary packets.
What is the success rate of cracking Wi-Fi with Aircrack-ng?
Success depends on several factors, such as the strength of the password, the quality of the wordlist, and the amount of data captured. For WPA/WPA2 networks, success is more challenging than cracking WEP.
Read Also: The Secret Linux Hacks Only Pros Know: Boost Your Productivity Today!







1 thought on “How To Use Aircrack-ng Tool In Kali Linux | Detailed Guide 2024”